📕 🤖 🔑 Managed Identities: A Practical Guide to Eliminating Secrets - from GitGuardian & CyberArk
5
📕 🤖 🔑 Managed Identities: A Practical Guide to Eliminating Secrets - from GitGuardian & CyberArk
5


Secrets Detection
Scan and fix hardcoded secrets in source code, CI/CD pipelines, and developer productivity tools – with GitGuardian’s secrets security platform.

Align developers, security teams, and DevOps engineers in a single platform.

Developers
Keep your code free from secrets
Scan every push and commit, find and fix hardcoded secrets while you code

SECURITY TEAMS
Enforce security policies for everyone, everywhere
Ensure every team is compliant and empowered to fix their own mistakes

CLOUD OPERATIONS
Get continuous pipeline security
Align engineering and security with automated secrets scanning in CI/CD

.svg)
.svg)
Scan locally, right in your dev environment (CLI or IDE).

Harden your pipelines with the ggshield CLI


.svg)
.svg)
.svg)



#1 app on
the GitHub marketplace














GitGuardian has absolutely supported our shift-left strategy. We want all of our security tools to be at the source code level and preferably running immediately upon commit. GitGuardian supports that. We get a lot of information on every secret that gets committed, so we know the full history of a secret.
Find out how GitGuardian reduces the risk of hardcoded secrets in your software supply chain
Source code
Continuously scan all public and private Git repositories listed under your GitHub, GitHub Enterprise, GitLab, or Bitbucket organizations.
Docker images
Scan your Docker images for hardcoded credentials before pushing them to public or private registries.
Developer productivity tools
Developers write more than code. Scan %external sources scanned for secrets% for hardcoded credentials.
Developer workstations
Set up pre-commit or pre-push hooks to scan source code on developer workstations with GitGuardian’s CLI, ggshield.
CI environments
Plug GitGuardian into your CI/CD and run secrets scanning automated tests in your pipeline.
Centralized Version Control Systems
Pull requests
Turn GitHub check runs on and scan every commit in your pull requests for hardcoded secrets.
High coverage with specific detectors
GitGuardian’s Mean-Time-To-Detect is a few seconds after the secret is publicly exposed.
Generic detectors
Capture JWT secrets, Bearer tokens, username/password pairs, and all types of high-entropy patterns not covered by specific detectors with GitGuardian’s “Paranoïd mode”. Our Machine Learning models analyze context, enabling you to classify and prioritize critical generic secrets.
Custom detectors
Define custom Regex rules for secrets specific to your organization.
High precision detection
Reduce alert fatigue with a %sdtpr%% True Positive Rate (TPR) and multiple occurrences grouping.
GitGuardian performs contextual analysis of the surrounding code to discard false positives and weak matches.
When possible, GitGuardian also checks the validity of the hardcoded secrets with non-intrusive HTTP calls to the host.
Developer alerting
Developers are at the forefront of the issue of secret leaks. GitGuardian alerts the developers involved in the incidents alongside your Security team.
Integrations
Connect GitGuardian natively to your SIEM, ITSM, ticketing systems, messaging apps, or configure your webhooks.
.svg)




Saved views for relevant incidents
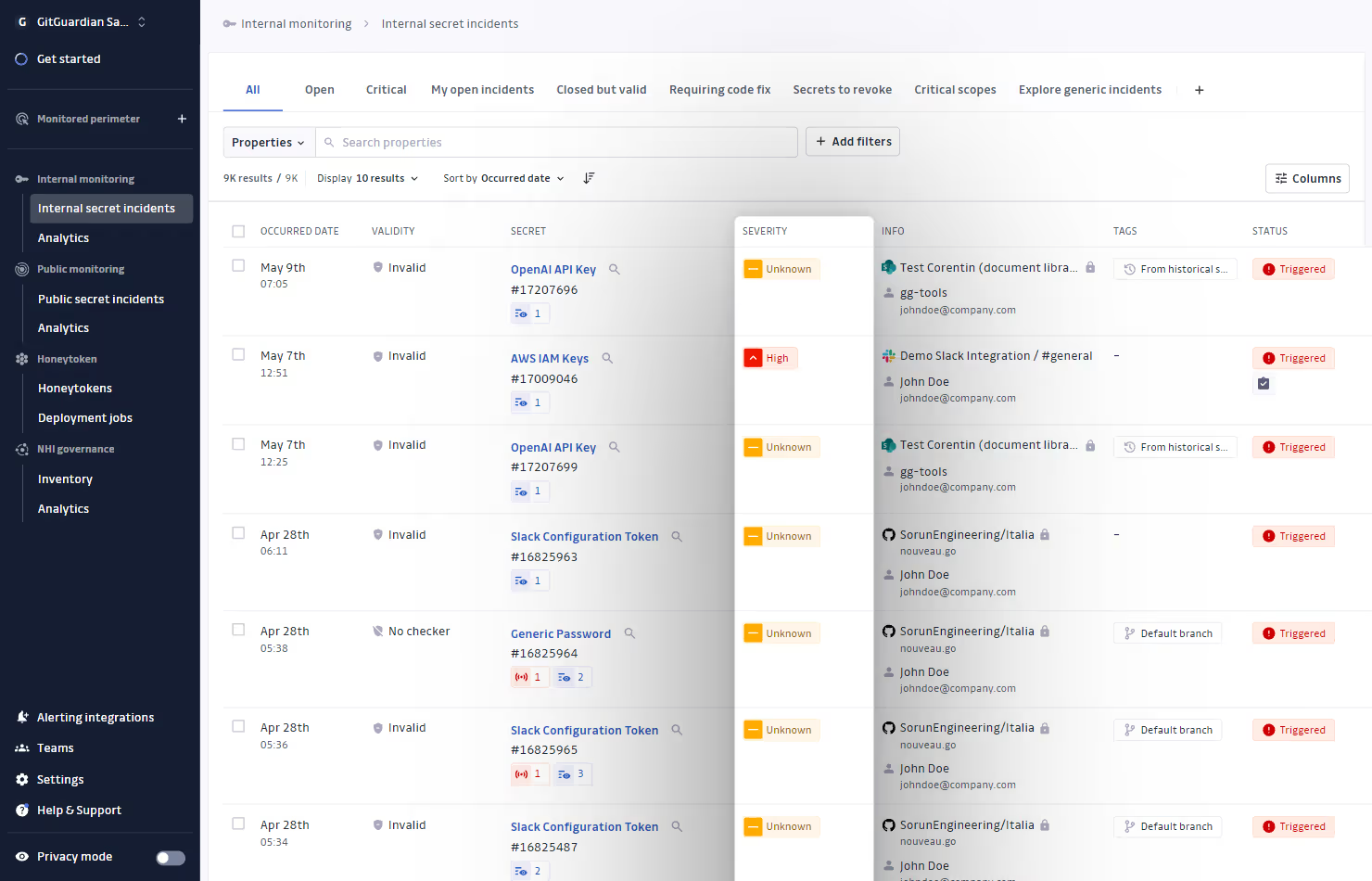
Save filter criteria to quickly display and share relevant incidents (e.g., “critical” incidents with “valid” secrets). Create views that align with your organization’s priorities.
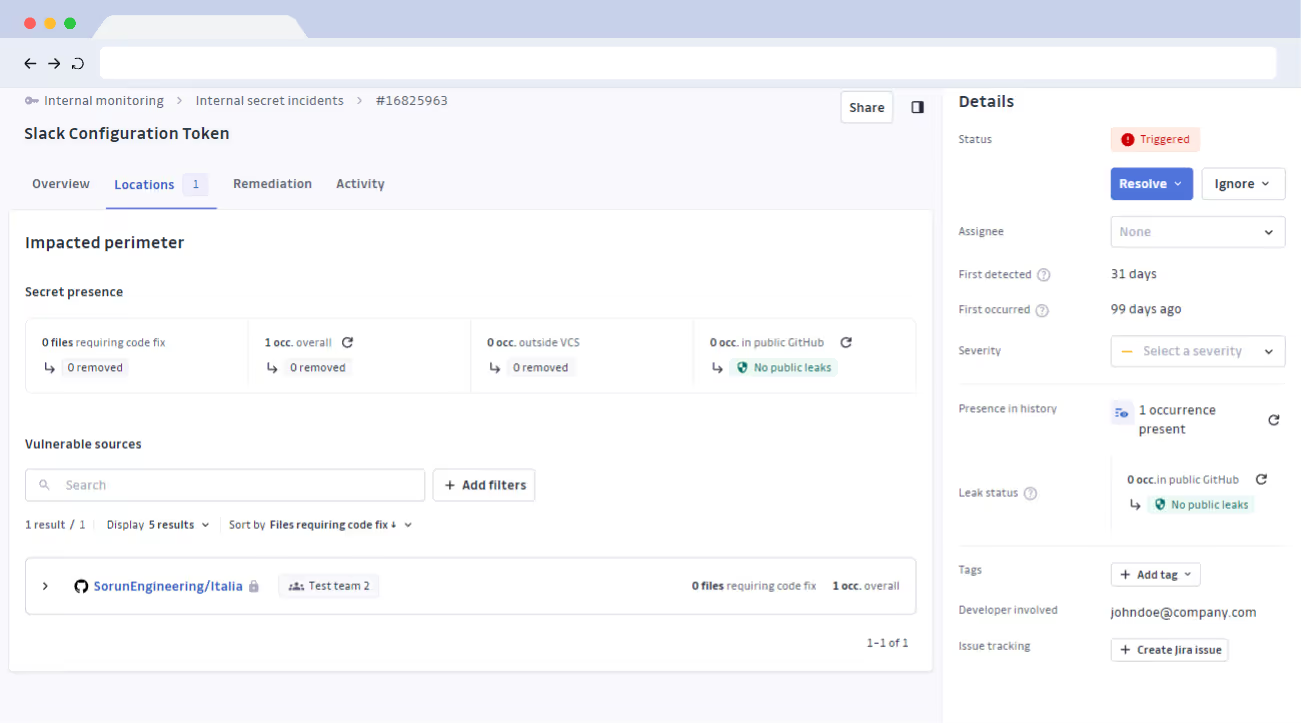
Incident prioritization
Explore and triage your incidents with key context information (secret type, location, incident severity, number of occurrences, live presence in the git repository, secret validity).
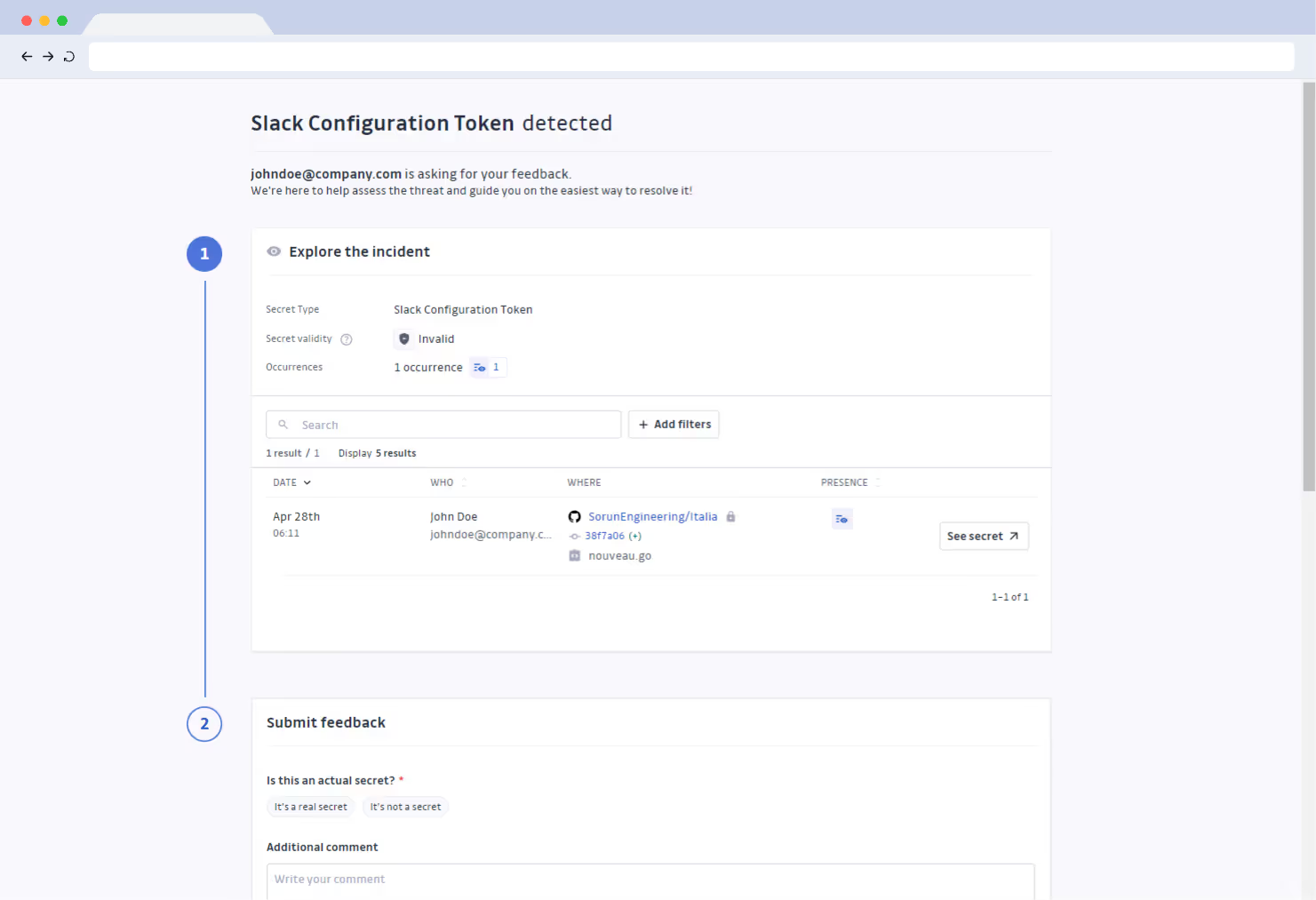
Developer feedback collection
Generate unique links to collect developer feedback on incidents. Harness the involved developers’ knowledge to understand the nature of the incident and the security risks it poses.
Developer-driven remediation
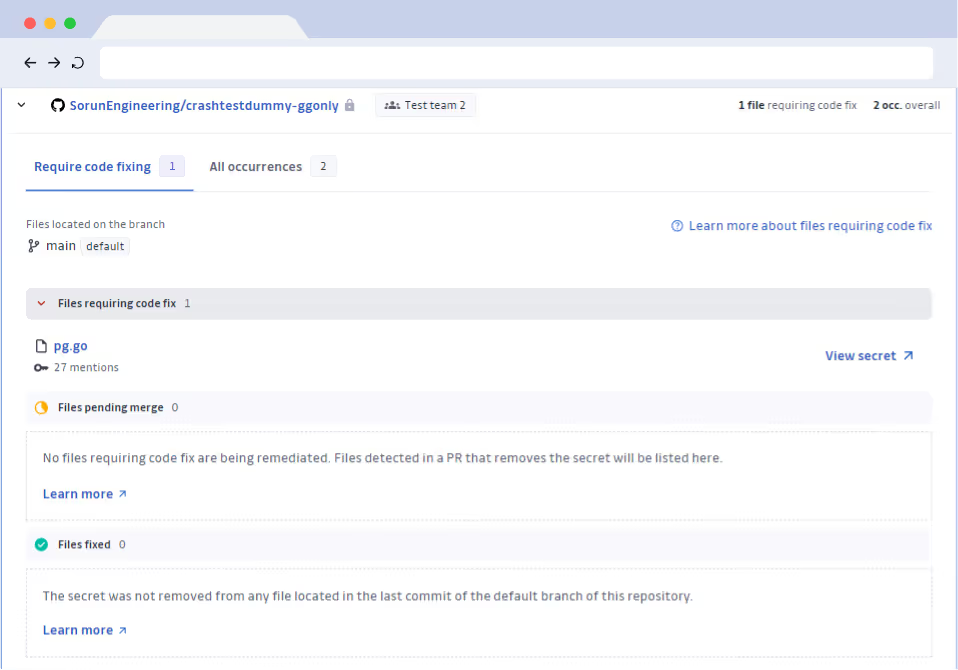
Empower developers to fix hardcoded secrets and resolve their incidents under your supervision.
Automated workflows
Enable automated playbooks for incident details sharing and developer-led remediation.
Programmatic incident management
Manage incidents programmatically with GitGuardian’s REST API.
SaaS implementation is available in the 🇪🇺 or 🇺🇸 zones
GitGuardian is GDPR-compliant with data storage in Frankfurt, Germany. Alternatively, data can be hosted on the East Coast of the USA.
Select the best region to fulfill your compliance and latency requirements.
Self-hosted option
GitGuardian can be deployed on bare metal, private or public clouds and can be deployed on existing Kubernetes cluster. It can be installed via a user-friendly interface or automated using Helm for a streamlined setup.
SSO
Single Sign-On functionality, compatible with any SAML 2.0 provider. Automate user onboarding and offboarding via SCIM.
Audit logs
Get detailed activity logs of all actions triggered on the dashboard or through the REST API.
RBAC
Control user permissions in the GitGuardian dashboard with "Admin", "Member" and “Restricted” roles.

And hide your secrets from the privy eyes of attackers.