
Table of Contents
Introduction: The Overlooked Complexity of NHI Lifecycle Management
TL;DR: Non-human identities lifecycle management is now critical as NHIs vastly outnumber human users, driving risks like secrets sprawl, orphaned credentials, and excessive permissions. Poor NHI governance leads to compliance gaps and major breaches. This article details top risks, OWASP guidance, lifecycle best practices, and how GitGuardian delivers end-to-end discovery, monitoring, and remediation across complex, multi-cloud environments. Read on for actionable strategies to secure your machine
Managing the lifecycle of Non-Human Identities (NHIs) is one of the most underestimated challenges in enterprise security. While Identity and Access Management (IAM) programs have matured significantly for human identities, enforcing onboarding, access control, monitoring, and offboarding processes, NHIs often lack the same level of governance.
NHIs now outnumber human identities by 45 to 100 times in large organizations, and with the rapid adoption of AI and low-code/no-code tools, this imbalance will only grow. Failure to manage their lifecycle introduces massive security and operational risks. These identities persist in CI/CD pipelines, cloud environments, and automation workflows, but without structured processes, they lead to long-lived shadow credentials, zombie accounts, excessive permissions, and fragmented governance.
As organizations grapple with the growing complexity of NHI lifecycle management, it's crucial to understand the security risks posed by unmanaged non-human identities. In the following section, we'll explore the potential consequences of failing to govern NHIs effectively.
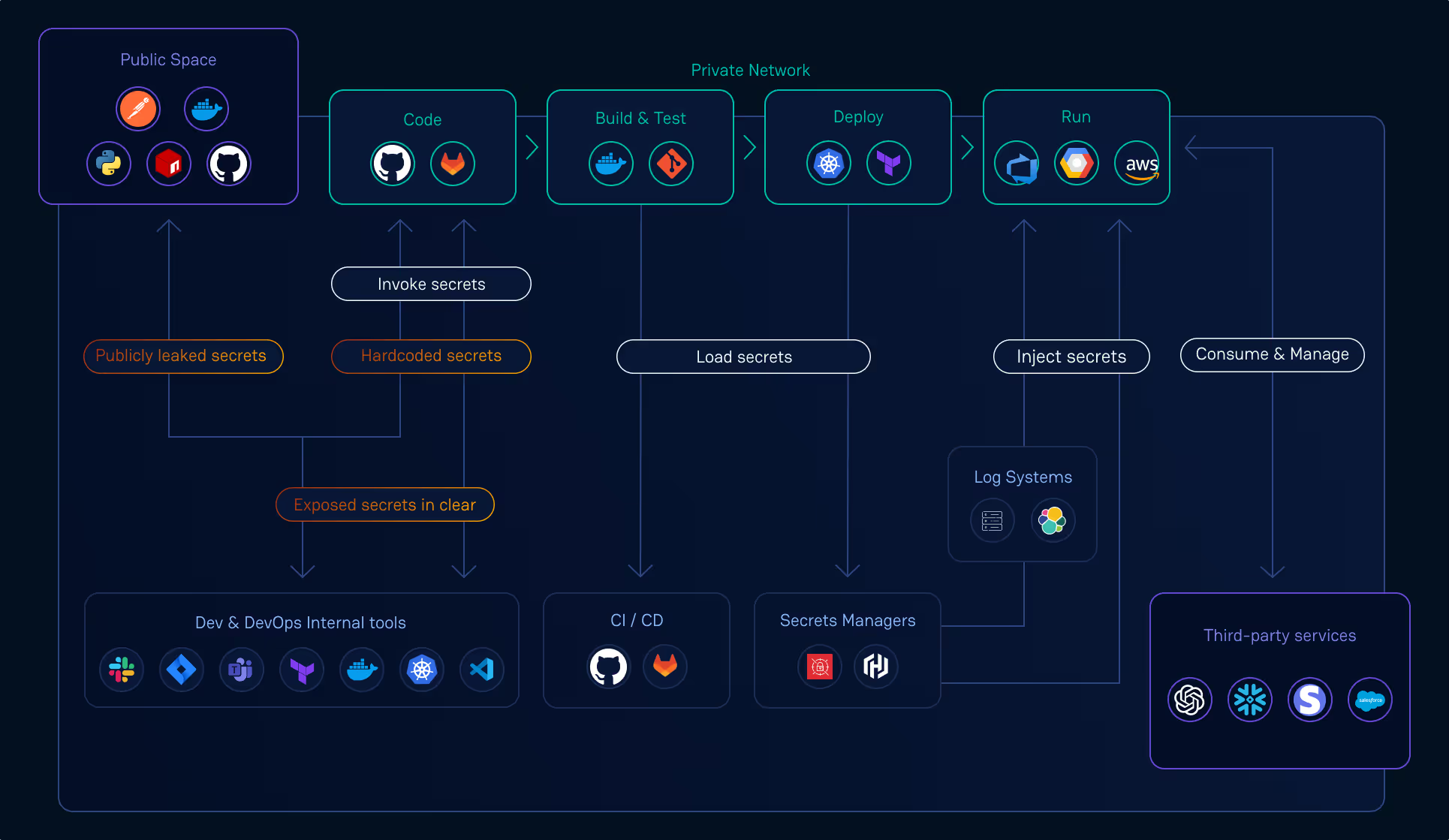
The TOP Security Risks of Unmanaged Non-Human Identities
When NHI lifecycles are poorly managed, organizations are exposed to a spectrum of security risks:
- Orphaned Credentials: NHIs that are no longer in use but still have active credentials provide attackers with a stealthy entry point. These "zombie" accounts often go unnoticed, allowing adversaries to establish a persistent foothold.
- Excessive Permissions: NHIs are often granted permissions that far exceed their intended use, violating the principle of least privilege and zero trust. Over-provisioned identities greatly increase the blast radius if compromised, enabling attackers to move laterally and escalate privileges.
- Secrets Sprawl: As NHIs proliferate, so do the secrets they rely on for authentication. API keys, tokens, and certificates end up scattered across public GitHub repositories, configuration files, ticketing systems, and CI/CD pipelines. This secrets sprawl dramatically expands the attack surface, making it easier for adversaries to find and exploit exposed credentials. The longevity of exposed secrets is alarming. GitGuardian's recent report reveals that 70% of valid secrets detected in public repositories in 2022 remained active in 2025, underscoring the persistent risks associated with leaked credentials.
- Lack of Visibility: Without a centralized inventory of NHIs and their relationships, security teams are blind to the web of machine-to-machine interactions occurring in their environment. This lack of visibility makes it nearly impossible to assess risk, proactively detect anomalies, or respond effectively to incidents. Devops teams also lack visibility when it comes to managing these identities for rotation, off-boarding, and deletion.
The risks associated with unmanaged NHIs are not merely theoretical; they have been recognized by leading industry experts. CyberArk’s “State of Machine Identity Security” report reveals that 50% of organizations reported security breaches linked to compromised NHIs in the past year. The Open Web Application Security Project (OWASP) has recently released a new framework that highlights the most critical security risks associated with machine identities.
OWASP Top 10 Non-Human Identity Risks for 2025
The Open Web Application Security Project (OWASP) has recognized the growing importance of non-human identities (NHIs) in the modern threat landscape. In response, they have released the OWASP Top 10 Non-Human Identity Risks for 2025, a new framework that highlights the most critical security risks associated with machine identities. This marks a significant milestone, as one of the most trusted cybersecurity communities acknowledges the unique challenges posed by NHIs and provides actionable guidance for mitigating these risks.
The Top 10 NHI Risks for 2025 are:
- Improper Offboarding: NHIs, such as access keys or service accounts, often persist long after they are needed, becoming forgotten targets for attackers.
- Secret Leakage: Compromised credentials are implicated in over 80% of breaches, underscoring the dangers of secrets sprawl.
- Vulnerable Third-Party NHI: Compromised third-party services with extensive access can infiltrate and compromise infrastructures and applications, enabling lateral movement and escalating the risk of data breaches exploitation.
- Insecure Authentication: Weak or outdated authentication methods, like long-lived API keys, put NHIs at risk.
- Overprivileged NHI: Machine identities are frequently granted excessive permissions, violating least privilege principles.
- Insecure Cloud Deployment Configurations: Hardcoded secrets in configuration files, especially in CI/CD pipelines, are low-hanging fruit for attackers.
- Long-Lived Secrets: NHI credentials without expiration dates provide attackers with long-term access if compromised.
- Environment Isolation: Reusing NHI credentials across development, testing, and production environments broadens the attack surface.
- NHI Reuse: Sharing NHI credentials across multiple applications or projects puts all dependent systems at risk if compromised.
- Human Use of NHI: Lack of controls around who or what can use NHI credentials makes it difficult to detect anomalous or malicious use.
These risks highlight the complexity of securing NHIs across increasingly interconnected and automated environments.
GitGuardian's platform is specifically designed to address the unique challenges of NHI security aligned with the OWASP Top 10 risks. By providing end-to-end visibility and control over NHIs through comprehensive discovery, contextual risk analysis, automated rotation and expiration, and continuous monitoring, GitGuardian empowers organizations to proactively mitigate risks outlined in the OWASP Top 10. This holistic approach to machine identity security is essential for protecting against the next generation of identity-based threats.

The Rise of AI and Its Impact on NHI Security
As organizations rapidly adopt AI-powered tools and autonomous agents, the number of non-human identities (NHIs) in enterprise environments is growing exponentially. While AI brings tremendous opportunities for efficiency and innovation, it also introduces new security risks and challenges related to NHI management.
AI agents, such as chatbots, virtual assistants, and automated decision-making systems, operate using secrets and credentials that grant access to sensitive systems and data. These NHIs can generate and consume large volumes of API keys, tokens, and other authentication mechanisms as they interact with various enterprise applications and services.
However, the rapid proliferation of AI-driven NHIs can lead to secrets sprawl, where credentials are scattered across systems, logs, and repositories. Without proper governance and visibility, these secrets become vulnerable to exposure and exploitation by attackers.
Moreover, AI agents often require broader permissions and access rights compared to traditional, deterministic bots. As these agents autonomously navigate complex systems and make decisions based on machine learning models, it becomes challenging to enforce least privilege access and maintain tight control over their actions.
Another significant risk stems from the use of prompt-based architectures in AI systems. When sensitive information, such as API keys or personally identifiable information (PII), is embedded in prompts or logs, it can lead to unintended exposure and potential data breaches.
The Limitations of Secrets Managers in Securing NHIs
While secrets managers like HashiCorp Vault, Cyberark, Delinea, AWS Secrets Manager, and Azure Key Vault are critical tools for securely storing and managing credentials, they alone are not sufficient for comprehensive NHI governance. Secrets managers address one facet of the challenge—providing a centralized, secure repository for secrets—but leave other critical aspects unaddressed:
- Discovery and Visibility: Secrets managers operate on the assumption that all secrets are properly stored within their confines. However, they provide limited visibility into secrets that may be hardcoded in source code, configuration files, scripts outside the vault, or even messaging or ticketing systems. This lack of discovery capabilities leaves a significant blind spot, as organizations cannot secure what they cannot see.
- Lifecycle Management: While secrets managers facilitate secure storage and access, they often lack granular controls for managing the full lifecycle of NHIs. On average an organization has 6 secret management instances in use across different teams or departments. This leads to fragmentation and complexity in managing secrets effectively. Functionalities like automated onboarding, continuous monitoring, and decommissioning of unused or stale credentials may be limited or absent, making it difficult to enforce consistent governance across all NHIs.
- Contextual Risk Analysis: Secrets managers primarily focus on the secure handling of credentials, but they don't provide deep insights into the context of how those credentials are used. Understanding factors like associated permissions, credential age, and usage patterns is crucial for identifying and mitigating risks like over-privileged access or anomalous behavior.
- Integration and Remediation: When secrets are discovered outside the vault, securely bringing them into the fold can be a manual and error-prone process. Secrets managers often lack automated workflows for detecting leaked secrets, triggering alerts, and guiding remediation efforts to ensure consistent policy enforcement.
This is where platforms like GitGuardian come in, complementing secrets managers to provide end-to-end NHI governance. GitGuardian bridges these critical gaps by:
- Continuously discovering secrets across code repositories, CI/CD pipelines, cloud environments, and secrets managers
- Providing contextual risk analysis to prioritize remediation based on factors like consumers, accessed resources and permissions
- Automating lifecycle management tasks, from onboarding to rotation and decommissioning
- Integrating with secrets managers to ensure seamless migration of discovered secrets into secure vaults
By combining the strengths of secrets managers and governance platforms like GitGuardian, organizations can achieve comprehensive NHI security, aligned with best practices and regulatory guidelines. This layered approach ensures that all NHIs are discovered, securely managed, and continuously monitored, reducing the risk of breaches and enabling zero trust architectures.
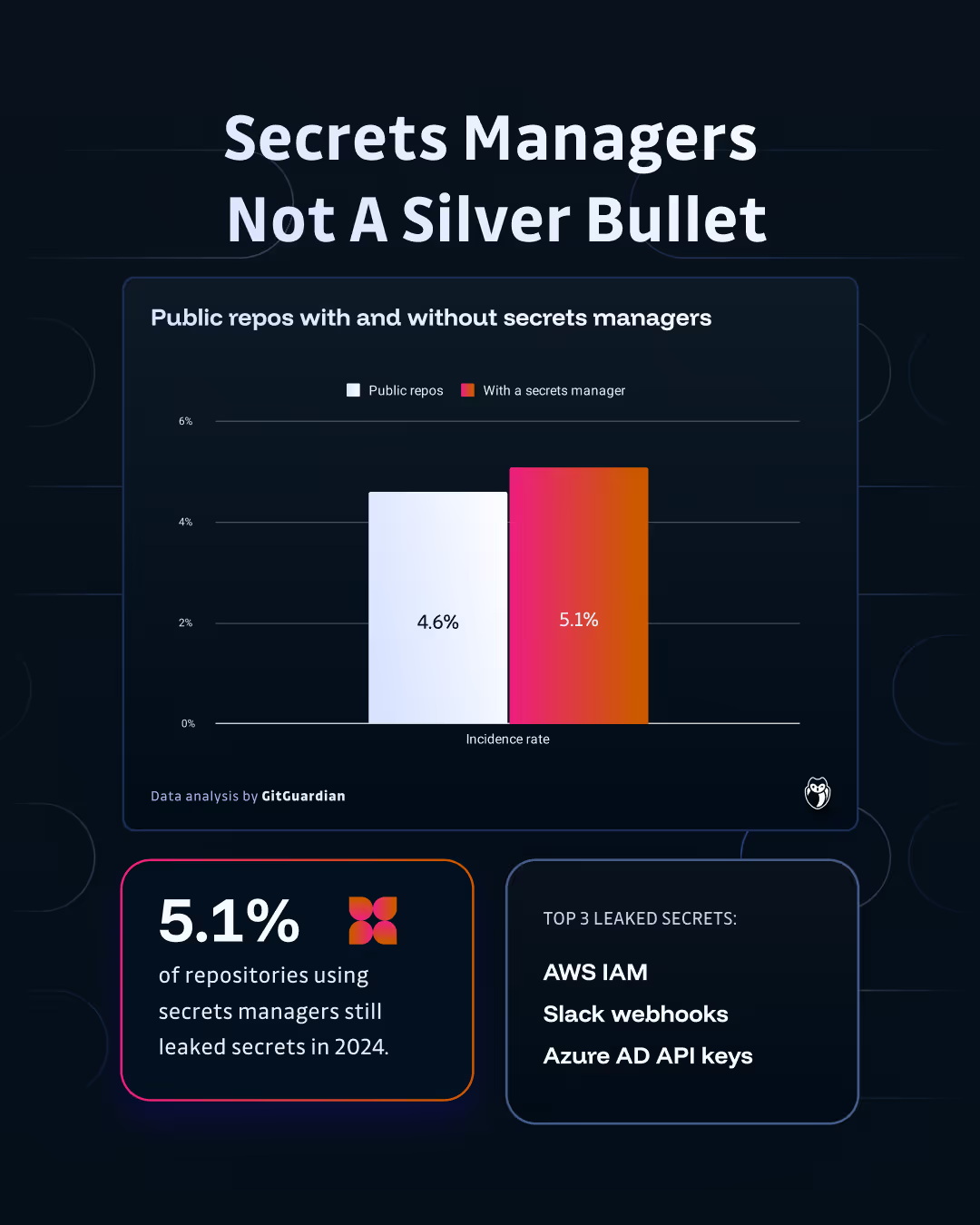
GitGuardian's analysis of public GitHub repositories using secrets managers found that 5.1% still contained leaked secrets, highlighting the importance of comprehensive NHI governance that extends beyond vault solutions
NHI Lifecycle Management: Key Steps and Challenges
https://blog.gitguardian.com/identity-lifecycle-management-for-nhis/
1. Discovery and Inventory
Effective NHI governance starts with a comprehensive discovery and inventory process. Organizations must identify and catalog all non-human identities across their enterprise, including service accounts, API keys, and certificates. Scraping data from multiple sources beyond just secret managers is crucial, as secrets can be manually created on servers, Kubernetes, or stored in places like GitLab. This involves mapping NHIs to their associated systems, applications, and services, as well as documenting ownership, purpose, and permissions.
Building and maintaining an up-to-date inventory of NHIs at scale is nearly an impossible task, especially in the face of rapid machine identity proliferation across complex, multi-cloud environments. Traditional manual approaches to NHI discovery often struggle to keep up with the dynamic nature of modern infrastructures, leading to incomplete or inaccurate inventories.
To overcome these challenges, organizations can leverage automated discovery solutions like GitGuardian. By continuously scanning repositories, CI/CD pipelines, and cloud environments, GitGuardian helps organizations maintain a complete and up-to-date inventory of their NHIs and associated secrets. The centralized inventory, enriched with contextual metadata, serves as a single source of truth for effective machine identity governance.
.avif)
2. Onboarding and Provisioning
With a comprehensive NHI inventory in place, the next step is to establish secure onboarding and provisioning processes. Standardized request and approval workflows, least privilege access enforcement, and integration with centralized secrets management platforms are key components of a robust provisioning strategy.
Inconsistent provisioning processes and manual workflows can introduce significant risks, such as misconfigurations and over-permissioned identities. These challenges can be addressed by adopting a centralized platform for managing NHI lifecycles to ensure consistency and reduce the risk of manual errors. Real-time visibility into permissions empowers organizations to maintain a secure and compliant NHI ecosystem.
3. Continuous Monitoring and Auditing
Continuous monitoring and auditing of NHI usage and behavior is essential for maintaining a secure environment. Tracking NHI activities across systems, identifying anomalous behavior, detecting policy violations, and generating detailed usage reports are critical tasks that enable organizations to stay on top of potential security risks.
The complexity and scale of modern distributed environments can make it challenging to achieve comprehensive visibility into NHI activities. With machine identities interacting with a wide range of systems and services, each with its own logging and monitoring mechanisms, correlating and analyzing NHI behavior can be a time-consuming and resource-intensive task.
When different teams use different secret managers, there is a risk of inconsistent practices and policies for managing secrets. This can lead to varying levels of security, compliance issues, and difficulties in enforcing standardized rotation schedules or access controls.
Platforms like GitGuardian streamline the monitoring and auditing process by providing a centralized view of NHI activities. By integrating with various systems and log sources, GitGuardian aggregates and normalizes usage data, enabling security teams to easily identify potential security incidents and policy violations. Advanced analytics and anomaly detection capabilities, coupled with customizable alerting, ensure that organizations can respond quickly to high-risk events.
4. Secret Rotation and Remediation
Regular secret rotation and remediation are crucial for maintaining the long-term security of NHIs. Automatically rotating secrets and credentials, remediating vulnerabilities and misconfigurations, and promptly revoking and replacing compromised or exposed NHIs are essential practices that organizations must adopt.
The importance of regular rotation and remediation is underscored by the CyberArk report, which found that 72% of organizations experienced at least one certificate-related outage in the last year, with 34% suffering multiple outages.
Managing secret rotation at scale can be complex, especially when dealing with dependencies between systems and applications. Inconsistent rotation schedules and the lack of a centralized management platform can lead to stale or expired credentials, increasing the risk of unauthorized access.
To simplify secret rotation and remediation, organizations can leverage solutions like GitGuardian that integrate with popular secrets managers. The platform's contextual insights help identify secret owners and streamline the remediation process, minimizing the potential impact of security incidents.
5. Decommissioning and Offboarding
Decommissioning and offboarding of unused or stale NHIs is a critical aspect of NHI lifecycle management. Organizations must have processes in place to identify and remove inactive NHIs, revoke their access and permissions, update inventory and documentation, and securely dispose of all associated secrets and credentials. Contextual insights and a clear understanding of secret dependencies are critical for efficient revocation and remediation processes.
Another challenge of decommissioning NHIs often lies in the lack of visibility into unused or stale identities, leading to the accumulation of "zombie" credentials that can be exploited by attackers. Fragmented tooling and inconsistent processes across teams can further complicate the decommissioning process, making it difficult to ensure that all NHIs are properly offboarded.
Centralized NHI lifecycle management platforms, such as GitGuardian, can help organizations overcome these challenges. By providing continuous discovery and monitoring capabilities, GitGuardian helps identify unused or stale NHIs that are candidates for decommissioning. Automated workflows ensure that access and permissions are revoked, while integration with secrets managers guarantees the secure disposal of associated credentials. With a unified view of the NHI lifecycle, organizations can maintain a clean and secure inventory of machine identities.
Implementing a comprehensive NHI lifecycle management program that addresses these key steps and challenges is essential for securing the modern enterprise. GitGuardian's platform offers the visibility, automation, and integrations necessary to effectively govern machine identities across complex, multi-cloud environments. By adopting a holistic approach to NHI management, organizations can reduce risk, ensure compliance, and unlock the full potential of their machine identities.
As organizations recognize the limitations of traditional secrets management approaches, many are exploring alternative solutions for securing machine-to-machine communication. One promising approach is the adoption of the Secure Production Identity Framework for Everyone (SPIFFE).
Measuring NHI Lifecycle Management Program Success
Establishing clear metrics and KPIs is essential for demonstrating the value and effectiveness of your NHI lifecycle management program. Unlike traditional identity programs that focus on user onboarding metrics, NHI programs require specialized measurements that account for the dynamic nature of machine identities and secrets sprawl.
Key performance indicators should include secrets detection coverage across your entire software development lifecycle, measuring the percentage of repositories, CI/CD pipelines, and cloud environments under continuous monitoring. Track mean time to remediation for exposed secrets, aiming for automated rotation within hours rather than days. Monitor orphaned identity reduction rates by measuring how many stale service accounts and unused API keys are decommissioned monthly.
Compliance metrics become critical for regulatory frameworks like PCI DSS 4.0, which now explicitly requires NHI governance. Track policy compliance rates across different environments, measuring adherence to least privilege principles and rotation schedules. Risk reduction metrics should quantify the decrease in high-risk secrets exposure, particularly those with administrative privileges or access to sensitive data.
Advanced organizations should measure developer workflow integration success, tracking how seamlessly NHI lifecycle management integrates with existing development processes without introducing friction. This includes monitoring false positive rates in secrets detection and measuring developer adoption of secure coding practices.
Cross-Platform NHI Lifecycle Orchestration
Modern enterprises operate across multiple cloud providers, secrets managers, and development platforms, creating complex orchestration challenges that traditional IAM solutions cannot address effectively. Successful NHI lifecycle management requires coordinated workflows that span AWS, Azure, GCP, HashiCorp Vault, Kubernetes clusters, and numerous SaaS applications.
The key challenge lies in maintaining consistent lifecycle policies across heterogeneous environments while respecting each platform's unique authentication mechanisms. For example, AWS IAM roles operate differently from Azure Managed Identities, yet both require synchronized lifecycle management to prevent security gaps. Organizations must establish cross-platform identity mapping that correlates service accounts, API keys, and certificates across different systems.
Secrets propagation tracking becomes citical in these environments, as a single service account might generate multiple secrets across various platforms. GitGuardian's approach addresses this through comprehensive scanning that follows secrets from their creation in code repositories through deployment in cloud environments, providing the visibility needed for effective cross-platform orchestration.
Automation workflows must account for platform-specific rotation requirements and dependency management. When rotating a database connection string, the system must understand which applications, containers, and services depend on that credential across multiple environments. This requires sophisticated dependency mapping and coordinated rotation schedules that minimize service disruption while maintaining security posture.
The Business Case for NHI Governance: Why CISOs Must Take Ownership
The financial and reputational damage from NHI-related breaches can be staggering. According to the CyberArk report, 77% of security leaders feel that every undiscovered machine identity (NHI) is a potential point of compromise. Beyond the immediate financial impact, breaches erode customer trust, tarnish brand reputation, and can even lead to executive turnover. In an age where every company is a software company, a major security failure can be an existential threat.
Neglecting NHI governance leaves a massive portion of the identity attack surface undefended. CISOs who fail to bring NHIs into their IAM strategy are exposing their organizations to significant risk.
The dangers of ungoverned NHIs are not theoretical. Numerous high-profile breaches have demonstrated the devastating consequences of inadequate machine identity management:
- The U.S. Department of the Treasury was breached through a compromised API key, granting attackers access to sensitive workstations and documents.
- Toyota exposed a long-lived access key to an internal data server, allowing unauthorized access to real customer data for 5 years.
- The New York Times exposed a GitHub token, resulting in 5,600 of their repositories being leaked online.
These incidents underscore the harsh reality: NHIs are a prime target for attackers. Secrets sprawl, long-lived credentials, and excessive permissions make machine identities low-hanging fruit for adversaries.
Beyond the immediate financial impact, breaches erode customer trust, tarnish brand reputation, and can even lead to executive turnover. In an age where every company is a software company, a major security failure can be an existential threat.
Compliance Mandates
As the threat landscape evolves, so too do regulatory requirements and security frameworks. Compliance mandates like PCI-DSS, GDPR, and ISO 27001, as well as NIST guidelines, increasingly emphasize strict access controls and least privilege enforcement—not just for human identities, but for machine identities as well.
Key sections of PCI DSS 4.0, relevant to NHIs became mandatory in March 2025 and include:
- Requirement 2: Enforce secure configurations for all system components, including NHIs, and eliminate default passwords.
- Requirement 7: Apply least-privilege access controls to NHIs to prevent excessive permissions.
- Requirement 8: Implement strong authentication mechanisms for NHIs, moving beyond static credentials.
- Requirement 10: Log, monitor, and audit all NHI activities to detect anomalies and ensure compliance.
NIST highlights the dangers of long-lived credentials, which provide attackers with prolonged access if compromised. Over-permissioned NHIs, which violate the principle of least privilege, further expand the attack surface. NIST also stresses the importance of continuous monitoring to detect anomalous NHI activity.
GitGuardian's capabilities directly align with NIST's and PCI DSS requirements for mitigating these risks:
- By continuously scanning repositories and CI/CD pipelines for hardcoded secrets, GitGuardian enables organizations to eliminate long-lived credentials and enforce strict policies for credential management.
- GitGuardian's advanced analytics help organizations identify overprivileged NHIs and optimize permissions based on the principle of least privilege.
- Through its integrations with secrets managers, GitGuardian enables the automated rotation and expiration of NHI credentials, drastically reducing the attack surface.
Organizations that fail to govern NHIs with the same rigor as human identities risk falling out of compliance. The penalties can be severe, including hefty fines, legal action, and even prohibition from operating in certain jurisdictions.
The Path Forward: A Unified IAM Strategy
DevOps and SRE teams often struggle with secrets sprawl, where credentials are scattered across multiple systems, such as secret managers, Kubernetes clusters, and version control systems like GitLab. This fragmentation makes it challenging to maintain a centralized inventory of secrets, track their usage, and enforce proper access controls. Moreover, the lack of a unified view of NHIs hinders the ability to correlate secrets across different sources, map dependencies, and efficiently respond to security incidents.
When a leak or compromise occurs, DevOps and SRE teams are tasked with revoking the affected secrets and remediating the issue. However, without a clear understanding of all the places where a secret exists, the revocation process becomes time-consuming and error-prone. This can lead to prolonged exposure and increased risk of unauthorized access.
To address these challenges, organizations must adopt a unified IAM strategy that empowers DevOps and SRE teams to effectively manage and secure NHIs. This requires investing in solutions that provide comprehensive secrets discovery, centralized visibility, and automated governance capabilities. By leveraging tools that can map relationships between secrets, enforce consistent policies, and streamline rotation and remediation processes, DevOps and SRE teams can reduce the burden of manual secret management and focus on delivering value to the business.
Moreover, fostering collaboration and knowledge sharing between DevOps, SRE, and security teams is crucial for implementing a successful IAM strategy. By working together to define best practices, establish shared responsibilities, and continuously improve NHI governance processes, organizations can build a culture of security that permeates all aspects of the software development lifecycle.
NHI Lifecycle Management in AI and Autonomous Systems
The proliferation of AI agents and autonomous systems introduces unprecedented challenges to traditional NHI lifecycle management approaches. These systems generate and consume identities at machine scale, often creating ephemeral credentials that exist for minutes or hours rather than months or years.
AI agent identity patterns differ fundamentally from traditional service accounts. Machine learning pipelines might spawn hundreds of temporary identities to access training data, process models, and deploy inference endpoints. Each AI agent requires its own authentication context, but traditional lifecycle management tools struggle with the velocity and volume of these short-lived identities.
Dynamic credential provisioning becomes essential, where identities are created just-in-time for specific AI workloads and automatically decommissioned upon task completion. This requires integration with container orchestration platforms like Kubernetes, where AI workloads frequently run as ephemeral pods with their own service accounts and secrets.
The challenge intensifies with AI model deployment pipelines, where the same model might be deployed across multiple environments with different identity requirements. Development, staging, and production environments each need isolated credentials, but the rapid iteration cycles of AI development can lead to credential sprawl if not properly managed.
Secrets in AI training data present another critical concern, as large language models and training datasets might inadvertently contain API keys or credentials. Continuous secrets scanning must extend to training data repositories and model artifacts to prevent credential exposure through AI outputs.
The Road to a Secrets-Free Future: Adopting SPIFFE for Machine Identity Management
As organizations embrace cloud-native architectures and the use of NHIs explodes, the challenges of securely managing machine-to-machine communication have become increasingly complex. Traditional approaches relying on long-lived secrets like API keys and hardcoded credentials are no longer sufficient. They introduce significant security risks, operational overhead, and developer friction.
Enter the Secure Production Identity Framework for Everyone (SPIFFE), an open-source standard for securely identifying and authenticating services in dynamic and heterogeneous environments. SPIFFE, along with its reference implementation SPIRE (the SPIFFE Runtime Environment), offers a path forward to a secrets-free future for machine identity management.
At its core, SPIFFE/SPIRE addresses the shortcomings of traditional secret-based authentication by leveraging short-lived X.509 certificates. Instead of relying on long-lived, static credentials, SPIFFE/SPIRE automatically issues and rotates certificates for each service, with lifetimes measured in hours or days rather than months or years.
This approach provides several key benefits:
- Reduced attack surface: With short-lived certificates, even if a credential is compromised, the window of opportunity for an attacker to exploit it is drastically reduced.
- Simplified operations: SPIFFE/SPIRE abstracts away the complexities of certificate management, automatically handling issuance, rotation, and revocation. This eliminates the operational burden of manually managing secrets across diverse environments.
- Improved developer experience: By offloading authentication and authorization concerns to the framework, developers can focus on building application logic rather than wrestling with secret management. SPIFFE/SPIRE provides a uniform, provider-agnostic API for service-to-service communication.
The path to adoption can seem daunting, especially for organizations with extensive legacy infrastructure and deeply ingrained secret management practices. However, GitGuardian's platform can help bridge the gap through a phased approach:
- Secrets Discovery: Gain a comprehensive inventory of all secrets currently in use across your environment.
- Centralized Secrets Management: Consolidate secrets into a centralized secrets management platform.
- Incremental SPIFFE/SPIRE Rollout: Selectively migrate services to SPIFFE/SPIRE, focusing first on the most critical or sensitive workloads.
- Continuous Monitoring: Provide ongoing scanning to catch and remediate any issues throughout the adoption process and beyond.
By embracing SPIFFE/SPIRE and committing to a phased adoption approach, organizations can progressively reduce their reliance on long-lived secrets and usher in a new era of secure, scalable machine identity management. The destination is in sight—it's time to take the first step.
Conclusion
The road ahead is challenging, but the risks of inaction are too great to ignore. Forward-thinking CISOs are implementing comprehensive NHI governance at enterprise scale. By discovering, managing, and securing machine identities with the same diligence as human identities, these leaders are forging a new path for IAM—one that recognizes the centrality of identity in the digital age.
The stakes could not be higher. In a world where every identity is a potential entry point, the organizations that can effectively govern the full spectrum of identities will be the ones that thrive. Those that fail to adapt will be left exposed to the next generation of identity-based threats.
The time for action is now. By prioritizing NHI governance, CISOs can secure their most critical assets, safeguard their reputations, and lay the foundation for a resilient digital future. The journey to comprehensive identity security begins with a single step—and that step must be taken today.






.svg)